Introduction
API integration platforms have become the backbone of the digital economy. They integrate applications, services, data, and cloud formats to extend automation and provide real-time data access. Most notably, the rise of e-commerce and cloud-based businesses has made it feasible to manage all of this behind the scenes, allowing businesses to remain adaptable and competitive.
APIs, by default, expose data and operations to the outside world. Without proper security controls, they may leave sensitive data and core infrastructure vulnerable. The more systems you tie together, the more you have at stake.
That’s the reason businesses should consider third-party security consideration as a fundamental requirement to build their API platform. Whether it’s identity verification or monitoring in real-time, the proper protections will keep your integrations from being your Achilles heel.
Here, we’ll explore the importance of API integration and the key security features every platform should have, the critical security must-haves that every API integration platform should deliver, and why each one matters more now than ever in a digital world that’s both high-risk and accelerated.
Why API Security Is a Business Problem: APIs Are Now Business-Critical Infrastructure
APIs are no longer the behind-the-scenes architecture; they’re the front door to data, apps, and services. The number of APIs and the resulting attack surfaces is growing as more businesses become more digitally connected. In fact, more than 50% of data breaches now come directly from exposed APIs, according to reports.
1. The real-world dangers of lax APIs

An improperly configured API could result in unauthorized access, stolen data, or even complete outages. Typical threats are credential theft, data exfiltration, and denial-of-service. These aren’t just downtime issues, they’re reputation-bashing, customer-trust-breaking, potential regulatory-fine accumulating problems.
2. One API Flaw, Many Well-Known Breaches

Some of the most widely-covered security events, ranging from attacks against banks, social media platforms, and SaaS p roviders, directly link to compromised API authentications, overly permissive access controls, and a failure to validate input. “An inch of deviation in API security opens them up to a mile of attack.
Also Read: Virtual Assistant Services in San Miguelito
3. The Importance of Built-in Security in API Integration Platforms

The Right API Platform Must Be Built with Security in Mind. When implementing an API integration platform, security must be considered from the outset. It must be designed with security-first practices to help counter new threats, support compliance, and reinforce long-term resiliency. When security is an afterthought, companies are exposed to significant, long-term operational and legal vulnerabilities.
4. The Business Benefits of Superior API Security

For businesses willing to invest in API platforms with security, they not only protect themselves but also earn their customers’ trust. Security reduces downtime, helps prevent breaches, and simplifies audits & certifications. In the API-first world of today, security isn’t just an IT issue, it’s a business enablement strategy.
Must-have API security essentials every integration platform should have
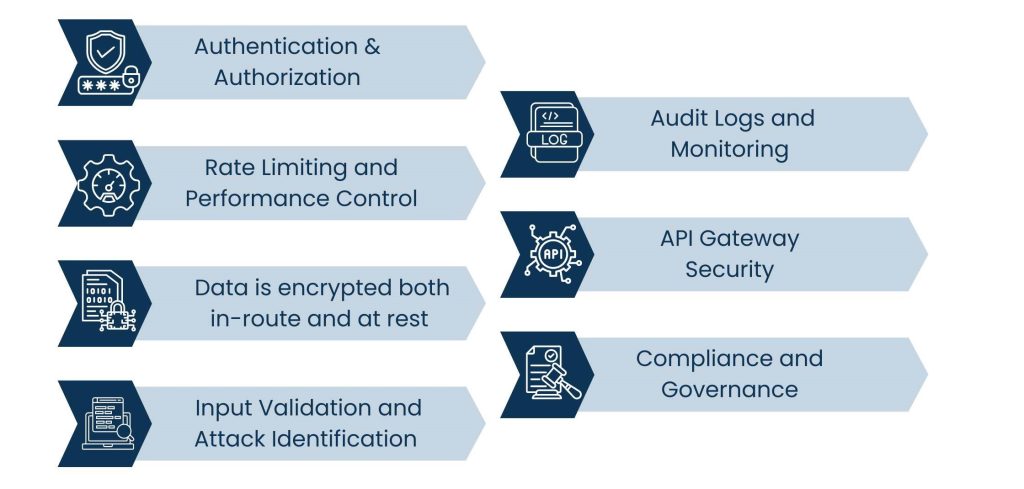
1. Authentication & Authorization
According to above mentioned principle processes, at the time of an attack, a user can disguise themselves as the other user or administer on another’s behalf.
Each API call includes identity authentication to ensure secure access. GitHub API integration platforms are considered secure when they implement token-based authentication protocols such as OAuth 2.0 or OpenID Connect. These systems would be able to facilitate access to only legitimate users and systems.
Authorization dictates what authenticated users are permitted to do. Access controls such as Role-Based Access Control (RBAC) and Attribute-Based Access Control (ABAC) enforce this by granting access only to actions that are required, thereby reducing the risk of unauthorized actions. Combined, these practices provide data privacy and operational work across the services.
2. Rate Limiting and Performance Control
API integration platforms need to set and adhere to rate limits to avoid abuse and DDoS attacks. Restricting helps prevent spikes in traffic that can destabilize the service and backend.
Good platforms are capable of special rules per IP/User/Token, balancing between fairness and security. These controls do likewise, helping to prevent abuse and preserve the user experience even in the face of high load.
3. Data is encrypted both in-route and at rest
There should always be encryption in transit and at rest of sensitive data. APIs implement TLS (Transport Layer Security) for securing transmitted data over the Internet.
Robust security standards such as AES-256 encryption for stored content help to protect your data against unauthorized access in the event of a security breach. It’s critical to invest in the right encryption to help ensure compliance and trust with partners and constituents.
4. Input Validation and Attack Identification
Untrusted inputs are the most common attack vector. All of the data has to be thoroughly validated by platforms at the edge to prevent injection attacks and broken requests.
Sophisticated API integration solutions keep an eye out for potential abuse, in real time. By integrating with threat detection products, you can identify and address threats before they develop into breaches.
5. Audit Logs and Monitoring
Transparency is key. Comprehensive audit logs allow teams to see who accessed what, when, and how, holding workers accountable.
Log retention policies and monitoring tools can also assist with incident response and forensic investigation. Investment in SIEM interoperability increases real-time visibility and threat response power.
6. API Gateway Security
An API gateway is the first line of defense when it comes to a properly configured one. It routes traffic, balances loads, and deploys . Also it enforces policies of security.
First class API integration platforms provide gateway functionality including IP filtering, SSL termination and rate limiting. These accoutrements thwart threats before they hit backend, and they add performance and resiliency.
7. Compliance and Governance
Security is not just about tech. Compliance with standards such as GDPR, HIPAA and SOC 2 not only protects users, but it also shields companies from heavy fines.
Governance capabilities are used to govern who can access information, enforce policies, and document conformance. These are the necessary tools to maintain your security posture and regulatory alignment across distributed teams.
Typical API Security Threats to Be Aware Of
The most powerful API integrations platform is just as secure as its ability to fend-off real-world threats. Once you have taken stock of the essential security capabilities that you will need, it is also worth discussing the kinds of attacks that such solutions will be able to defend against. Here are four of the most widespread and dangerous risks that go straight for APIs, and what makes them so crucial to tackle.

1. Broken Object Level Authorization
This is one of the most frequently abused API vulnerabilities. That happens when APIs don’t check that asked user should even have access to an object, a database record, or a file. A malicious actor could manipulate the identifiers into something else (ex, id in a URL) to query data you don’t want them to access. To prevent this, API integration platforms need to have strong authorization checks in place on each request.
2. Injection Attacks
Injection flaws occur when untrusted data is sent to an interpreter such as SQL, NoSQL, or even XML. This input can change the meaning of the API and cause harm. These attacks can subject backend data to be expose, modify, or destroyed. The best way to counter this is that platforms should sanitize their inputs and have a good input validation process.
3. Man-in-the-Middle Attacks
In MitM, an attacker sits between two communicating devices, you can capture their credentials, session tokens, or any other data that is flowing to and fro. This is most commonly due to insecure API endpoints or missing encryption. API gateways are supposed to force HTTPS with TLS (this is non-negotiable), and they should also be aware of token misuse to thwart these kinds of interceptions.
4. Excessive Data Exposure
A lot of APIs will return lots of data, where the client-side is tasked with filtering what gets displayed. This poses a threat since any third-party connecting to the raw API response can steal sensitive information. The top platforms architect their endpoints to deliver a “just what is needed” minimum set of data, and apply field-level encryption or sanitization as necessary.
Being aware of these threats is key to developing or selecting a secure API integration solution. It’s not just about having features, but how effectively they counter real-world attack patterns. The ideal platform not only has security features, but is designed to protect you against the worst types of threats in the API economy.
Security Nature of Teams with API Integration Platforms
No matter how secure an API platform is, internal teams play a critical role in system and data defense. Security doesn’t end at the platform level, it’s a team sport across development, operations, and security. Here are the critical best practices every organization needs to do to harden their API use and minimize risk.

1. Implement Least Privilege Access
Provide users, applications, and services with the least amount of access needed at all times. This mitigates the impact of compromised credentials or stolen tokens. Leverage RBAC and monitor permissions regularly.
2. Rotate API Keys and Secrets Frequently
Hardcoding or using expired API keys is a very large vulnerability. Store secrets safely in environment variables and secret management tools. Establish automation to both rotate keys on a schedule or at the detection of a security event.
3. Leverage Strong Authentication and Token Policies
Where available, use multi-factor authentication (MFA) and ensure access tokens have short expirations. Use ephemeral tokens, scoped to a particular resource or action.
4. API Traffic to and From the API – Secure And Track
Internal traffic should be encrypted via TLS, too. Implement logging and monitoring to notify of abnormal behavior, such as too many requests, unauthorized endpoints, or unsuccessful authentication.
5. Adopt a DevSecOps Mindset
Security needs to be built in at every stage of development. Engage security folks with design and code reviews. Perform static and dynamic security testing (SAST/DAST) of your APIs as part of your CI/CD pipelines.
6. Preserve a shared responsibility model
Explain how your team will need to work together to implement the various features of API security. Document and communicate responsibilities, so that coverage isn’t forgotten and missed through assumptions.
Through these internal security best practices, companies can greatly minimize exposure, even amidst very vulnerable API environments. But discipline, automation, and the culture of a team matter just as much as the built-in protection of the platform.
Also Read: Virtual Assistant Services in Santiago
Security Across the API Lifecycle: From Design to Decommission
API security is not a one-time effort, it is a continuous task that needs to be integrated at every phase of the API lifecycle. From its conception and with its build-out to closing, measures need to be taken to prevent misuse and keep pace with the system.

1. Design Phase
Begin with the secure-design principles. Decide what information is visible, who should have seen it, and how you’ll control access. Apply threat modeling to find potential holes in the system early on.
2. Development Phase
Validate input, monitor those error messages carefully, and don’t manually insert
secrets as you code. You should log everything and make sure you do not leak any sensitive information in your debug messages or responses.
3. Testing Phase
Run an automated scanner to look for vulnerabilities. Perform penetration tests and fuzzing for malicious code to see how your application responds. Check how an API handles incorrect or random data.
4. Deployment Phase
Have the API gateway and reverse proxies brought up securely. These should encrypt all traffic, police rate, authenticate, and control access. Leverage versioning to prevent breaking changes or activating legacy endpoints.
5. Maintenance Phase
Regularly review usage and audit logs. Address security alerts as they come in and fix vulnerabilities immediately. Re-evaluate the exposure of your API on a regular basis and update your polices as new risks emerge.
6. Closing Phase
Retire unused APIs properly. Disable access, revoke tokens, securely archive logs, and notify dependent systems. No deprecated endpoints should be left accessible or undocumented.
Looking into securing APIs through their life cycle, you make sure you aren’t just reacting to the threats but are perpetually one step ahead of them. This lifecycle-aware mindset is critical in crafting resilient systems in an API-first world.
Conclusion
API integration platforms security is no longer a nice-to-have, it’s an absolute necessity. As platform tools that support the integration of APIs (Application Programming Interfaces) power everything from payment gateways to customer data flows, the land of possibility expands as quickly as the land of risk. So whether you are exposing your own APIs or connecting to third party services, every endpoint is a doorway into your systems.
Thankfully, there is a way to manage these risks, but only if security becomes a priority and not an afterthought. That includes choosing platforms that are layered in security from the ground up, and ensuring your teams are trained, preemptive, and empowered to perform their roles.
Those businesses that make API security a business priority (not just a development priority) stand above the rest in terms of stability and customer confidence. From authentication protocols and data encryption to lifecycle governance and team discipline, all layers compound for a strengthened, more robust system.
Your weakest API within your ecosystem can become your liability (or your best asset). The choice lies in how you fasten it.
At Tasks Expert, we have a specialized team of professionals who can integrate an AI platform with compliance and ensure your safety. They offer personalized services, tailored to your unique needs. Contact us today to make your API platform secure and compliant.
About Us
Tasks Expert offers top-tier virtual assistant services from highly skilled professionals based in India. Our VAs handle a wide range of tasks, from part time personal assistant to specialized services like remote it support services, professional bookkeeping service etc. Furthermore, it helps businesses worldwide streamline operations and boost productivity.
Ready to elevate your business? Book a Call and let Tasks Expert take care of the rest.